WinZip
Learn the most common mistakes leading to data breaches, their repercussions, and how you can avoid them.
The cyber threat landscape of today looks very different from how it did five years ago and how it will look five years from now.
Cybercrime has become a profitable business, and cybercriminals are constantly working to hone their craft and take advantage of the newest technologies and techniques.
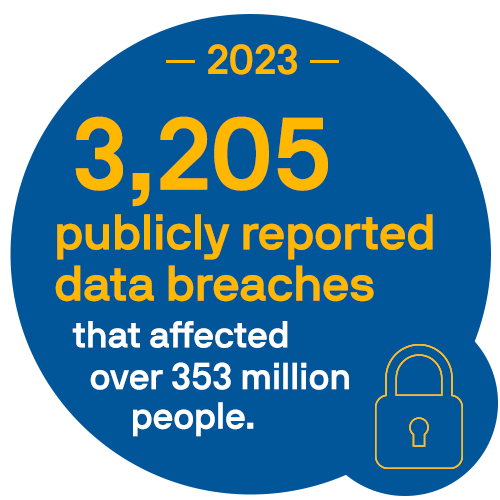
In 2023, there were 3,205 publicly reported data breaches that affected over 353 million people. Some of these breaches were the result of sophisticated cyberattacks by advanced persistent threats. Others were the cybersecurity equivalent of leaving the front door unlocked and the box for some expensive new gadget sitting on the curb.
Protecting against these threats requires an understanding of all the ways that data security can go wrong.
This report explores the most common mistakes that lead to data breaches, their repercussions, and how you can avoid them.
Data breaches are bad. Assuming that the company’s still standing afterward, it takes a lot of time, effort, and resources to pick up the pieces and return things to normal. These are some of the many ways in which poor data security—leading to a data breach or data destruction—can hurt the company.
Data is a valuable asset, both to companies and the cybercriminals attacking them. Often, the primary purpose of a cyberattack is to steal data or destroy it in order to hinder an organization’s operations.
A prime example of this is ransomware, which has recently evolved to do both. In the past, ransomware would encrypt data, demanding a ransom for the decryption key needed to restore it. Now, ransomware groups are increasingly stealing the data as well, threatening to leak it if their victim doesn’t pay up.
While a data breach doesn’t necessarily mean that a company loses access to its data, data destruction can have devastating impacts on an organization. A prime example of this is the attack by the Industroyer malware on the Ukrainian power grid. A December 2016 attack considered a test of the malware caused one-fifth of Kyiv to lose power for about an hour.
One thing that’s true of nearly every data breach is that it’s expensive for its victims.
In 2023, the average cost of a data breach was $4.45 million. Companies can lose money due to a breach in various ways, including:
In reality, any company can be the victim of a data breach if the attacker has enough knowledge, patience, and resources. However, the common perception is that data breaches only happen to companies that have committed significant security blunders. While often true, this isn’t always the case.
Fair or not, the perception that a company failed to protect its customer data can cause significant damage to the brand. In some cases, this can cause customers to go to a competitor or may force the company to spend significant sums repairing its damaged image.
Data breaches can have short-term and long-term impacts on an organization’s ability to do business. In the short term, a ransomware attack or similar incident can incapacitate an organization.
For example, a 2023 ransomware attack against Ardent Health Services—a healthcare chain with 30 hospitals—forced the organization to send patients to other emergency rooms and postpone elective surgeries since critical data and systems were rendered unavailable by the hack.
In the longer term, the brand damage caused by a successful data breach can result in lost business as well. While many customers won’t follow through on their threats to stop doing business with a company after a breach, even the small percentage that do represents a significant amount of lost revenue.
While some data breaches might be considered unavoidable, others are made possible through negligence by the company.
In these cases, companies may face class action lawsuits and other legal action by the victims of the incident.
Companies may also face legal and contractual penalties after a security incident if it causes the company to breach its service level agreements (SLAs).
For example, a ransomware attack could cause downtime that forces the company to pay restitution to the customers if it couldn’t provide contracted services.
Data protection laws such as the European Union’s General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS) are designed to protect customers' data from being breached.
If a company is the victim of a breach, then regulators may be taking a long, hard look to see whether they were doing enough to try to prevent it.
Most regulations lay out a set of minimum security controls that an organization needs to have in place to protect certain types of sensitive data. These include encryption, access controls, firewalls, and various others.
If the victim of a breach is compliant but warrants further investigation, then a post-breach audit may be necessary.
However, post-incident investigations of data breaches commonly reveal systemic flaws within the organization’s data security program.
One example of this is the Equifax hack, which exposed the personal financial data of about 147 million people. This hack was made possible by a failure to patch a vulnerability in Apache Struts—a widely-used framework for creating web applications—that was known to be actively exploited and went undetected because a critical security tool’s digital certificate expired ten months earlier.
As a result of the breach, the U.S. Federal Trade Commission imposed a fine of $700 million on the company.
In theory, data breaches should rarely happen. With strong encryption, robust access controls, trained employees, and the right security controls in place, a company can make it difficult and unprofitable for a cybercriminal to steal and leak sensitive data.
However, there were an average of 61 data breaches each week in 2023. The reason for this is that most companies don’t have all their ducks in a row with regard to data security. Errors in access management, cryptography, and data retention and deletion are some of the leading causes of data breaches.
By definition, a data breach is a failure of access management. Data is only considered breached if someone who isn’t supposed to have access to the data gets it anyway.
While data breaches are caused by various reasons, nearly three-quarters involve a human element. This largely involves employees making mistakes, which is why employee training is so essential to effective data security.
This section looks at some of the most common ways that access management failures lead to lost or destroyed data.
Passwords are the most common tool for controlling access to sensitive data, but they’re horrible at their job. In fact, 49% of data breaches involve stolen credentials.
Often, passwords are easily guessable by attackers or reused across multiple accounts, making it so that a single breach compromises all related accounts.
Of course, this assumes that passwords are used at all and that sensitive data isn’t accessible to anyone who stumbles across it.
One famous example of a data breach potentially caused by weak passwords is the SolarWinds hack. This incident affected hundreds of companies after attackers gained access to SolarWinds’ development environment and pushed a malicious update to its SolarWinds Orion network monitoring product.
In 2019, it was discovered that an intern had set their account password to “solarwinds123” back in 2017 and posted that password on a private GitHub account that accidentally leaked it publicly.
This account had the ability to upload files to SolarWinds’ servers and add them to an update. While it’s not certain that this was the cause of the hack, it did provide the necessary access and capabilities.
Defining access controls is a common struggle, and organizations often err on the side of too much rather than too little. It’s easier to give everyone all of the permissions that they could possibly need rather than tailoring the access to the role.
This is even true of external partners, as 72% of companies grant third parties sufficient access to perform full account takeover of their cloud accounts.
This problem is so prevalent that the zero-trust security model was created solely to state that maybe not everyone in the organization needs access to every file and system on the corporate network.
In 2023, Microsoft suffered a breach in which attackers were able to access and monitor top executives’ email accounts for months. This attack was made possible by guessing the password of a legacy test account that was inappropriately assigned admin-level access.
With this access, the attacker was able to create a malicious application and use OAuth—the protocol that underlies “Sign in with Google” and other options for granting access to users’ data—to assign full rights to email accounts, enabling it to read the executives’ emails.
The cloud is designed to make file storage and sharing easy. Many cloud platforms offer link-based file sharing that allows anyone with the link to access the file.
However, while this is very convenient, it’s also a major data security risk. Attackers can guess these links, and they can be sent to unauthorized recipients. Publicly-shared documents can be forgotten after they are no longer in use.
In 2023, Microsoft suffered a 38TB data breach due to a public cloud link. The company’s AI research division had a public GitHub repository that provided access to certain images and code from the company’s Azure Storage bucket via a Shared Access Signature (SAS) token.
However, this token was misconfigured to give full access to the bucket in question rather than the open-source images and code intended to be shared.
As a result, sensitive information was exposed; however, this luckily did not include any customer data.
Email chains can get long and complicated, and it can be difficult to verify that everyone on the chain is authorized to view an attached document. It’s also easy to accidentally send an email to the wrong person, or an existing email can be forwarded to a third party.
All of these scenarios pose the risk of exposing sensitive information to an unauthorized recipient. They also run the risk of putting an organization in hot water with regulators.
For example, under the Health Insurance Portability and Accessibility Act (HIPAA), emailing protected health information (PHI) to the wrong person can be a reportable breach.
The impacts of an email address typo can vary, but one 2023 accident was about as bad as it gets. The UK’s Ministry of Defence launched an investigation after discovering that classified information was sent to Mali—a Russian ally—rather than the U.S. Department of Defense (DoD).
This classified data leak was made possible by a simple typo. The U.S. DoD has email addresses with the .mil top-level domain (TLD), while .ml is a TLD assigned to Mali. A single missing ‘i’ was all it took to redirect these sensitive emails.
Shadow IT is the practice of employees using unauthorized devices, software, etc., for business purposes. With the growth of cloud computing and software as a service (SaaS) solutions, cloud environments have become a common source of shadow IT.
If employees upload corporate data into personal cloud storage or SaaS apps, the company loses visibility into and control over it. This creates the potential for data to be breached due to insecure personal cloud environments or for employees to take data with them when they depart the company.
A 2023 breach of Okta that affected several of the company’s customers—including 1Password, BeyondTrust, and Cloudflare—was attributed to the use of a personal Google account on a corporate laptop.
An employee who logged into their Chrome browser with a personal account saved the credentials for the service account of the corporate customer support system in Chrome’s built-in password manager.
After compromising the user’s personal account and stealing these cached credentials, the attacker was able to steal session tokens from Okta’s customer support system and perform session hijacking attacks.

Parallels®️ RAS (remote application server) is a flexible virtual application and desktop delivery solution that empowers organizations of all sizes to work securely from anywhere, on any device. To ensure confidence in deployment confidence, regardless of configuration, exceptional end-to-end security and compliance measures are built directly into the Parallels RAS code. With flexibility, simplicity, user experience and cost-efficiency at the top of its mind, Parallels RAS enables companies all over the globe to make secure remote access a possibility.
Learn moreEven if data stays in the corporate cloud environment, there’s no guarantee that it will be properly protected against exposure.
Corporate cloud environments can also have security misconfigurations, access control vulnerabilities, and other issues that expose them to attack. In fact, Gartner estimates that 99% of cloud breaches through 2025 will be the customer’s fault.
One famous example of a breach due to cloud misconfigurations is the Capital One breach of 2019. This attack was performed by a former AWS employee who attacked Capital One’s account to steal the financial data of about 106 million Capital One customers.
The Capital One breach was a server-side request forgery (SSRF) attack against Capital One’s web application firewall (WAF). The attacker tricked the WAF into performing HTTP requests on their behalf to Capital One’s AWS systems.
In this case, the problem was the fact that a misconfigured WAF had the ability to read all of the data in the company’s AWS account. The attacker abused this access to leak customer data, which they later posted online, leading to the attack being detected and their arrest.
Cryptography stands tall as the champion against breaches. Encrypted data is like an impenetrable fortress, safeguarding your sensitive information from prying eyes – that is, if you wield the cryptographic sword with finesse!
Here's the catch: the magic of cryptography works only when the incantations are right and the keys are guarded with utmost care.
Here are some of the ways that cryptography goes wrong:
The easiest way to mess up data encryption is to not encrypt data at all. Regulations such as GDPR, PCI DSS, and HIPAA mandate that certain types of data should be encrypted. However, a significant percentage of sensitive data remains unencrypted and under-protected.
These shortcomings can occur for various reasons. An organization may not be aware that it has data that needs to be encrypted. Or it may be stored in cloud environments, which may lack built-in encryption. In fact, only about 45% of data stored in the cloud is encrypted.
Data breaches of unencrypted, highly sensitive data are—unfortunately—common. One example from 2023 involved the travel giant Mondee and its subsidiary TripPro. About 1.7 TB of data hosted on the Oracle cloud was unencrypted and not password protected. The unsecured data included customers’ names, genders, dates of birth, home addresses, passport numbers, flight information, and credit card numbers.
This exposure allowed anyone to access the sensitive data inside using a web browser, just with its IP address.
A secure cryptographic algorithm provides strong data protection, while a weak one only creates a false sense of security. In some cases, a developer might attempt to create their own encryption algorithm; however, this is much harder than expected.
In fact, even seasoned cryptographers make mistakes in designing cryptographic algorithms. In 2022, SIKE—a cryptographic algorithm that made it to round four of NIST’s contest for post-quantum cryptographic algorithms—was broken. The researchers found that they could crack keys protected by the algorithm in a little over an hour.
A more common mistake is to use cryptographic algorithms that were previously secure but have since been broken.
For example, the Data Encryption Standard (DES) used to be the gold standard for encryption. However, it has been broken since 1999 and was replaced by the Advanced Encryption Standard (AES) in 2001.
A failure to perform regular encryption audits—verifying that secure algorithms are being used correctly—can allow major errors to slip through the cracks.
In 2020, a report by Citizen Lab found that Zoom was using AES-128 in electronic codebook (ECB) mode rather than AES-256 as they claimed. While AES-128 is secure, ECB is a broken algorithm for any message over 128 bits long. With ECB mode, identical 128-bit blocks of data produce identical ciphertexts, enabling attackers to make guesses regarding their contents.
Cryptography is powerful but fragile if not designed and implemented correctly. Using the wrong cryptographic algorithm or even making small configuration mistakes can undermine the protection provided by the cryptography. That’s why having a robust encryption solution is of utmost importance.
One common mistake when implementing cryptography is reusing certain values that should be unique for each encrypted value. Initialization vectors (IVs), nonces, and similar values need to be unique to ensure that identical plaintexts produce different ciphertexts and to protect against certain cryptanalytic attacks.
Tencent’s Sogou Input Method — a popular Chinese language input app for Windows, iOS, and Android — suffered a 2023 data breach due to misuse of encryption. The application was vulnerable to a cipher block chaining (CBC) padding oracle attack that would allow an attacker to decrypt network traffic, which could contain sensitive information.
Data can be encrypted in various ways. One of the most common options is disk-level encryption, which encrypts the entire contents of a disk with a single key. When an authorized user logs in, the disk is decrypted, making it available for use.
The problem with disk-level encryption is that it’s all-or-nothing. Once a user has logged in, all protection is stripped away from the data on the computer. A compromised password or a vulnerable application can provide access to the data while bypassing disk-level encryption.
Any attack exploiting a web application vulnerability like SQL injection bypasses disk-level encryption.
For example, disk-level encryption is enabled by default in Google Cloud Platform GCP. However, a 2023 vulnerability in GCP’s Cloud SQL service could have exposed data stored on the platform. The vulnerability allowed an attacker to escalate their privileges on the system, eventually resulting in full sysadmin access.
Companies are subject to a range of data retention and deletion requirements. Data privacy laws want companies to minimize the customer data that they hold, while other laws mandate the retention of certain records.
Attempting to comply with these requirements—successfully or otherwise—can create security risks if an organization lacks clear, regularly reviewed policies.
Here are some examples:
Data storage has become much cheaper in the last few years. Cloud storage costs are about $0.02 per GB per month, and most cloud accounts come with gigabytes of free cloud storage.
For this reason, there’s little or no financial reason to delete data even when it’s no longer needed.
Additionally, companies may—and should—create frequent backups to protect against ransomware, data loss, and other threats.
However, abandoned and forgotten data in cloud environments can pose a significant security risk. These datasets may include sensitive information and may not be protected as strongly as they should be.
As a result, attackers may be able to access under-protected data and use it to attack a company and its customers.
Additionally, the company also faces potential regulatory penalties under the GDPR and similar laws that mandate the deletion of customer data after it is no longer needed.
In 2021, DNA Diagnostic Center (DDC)—a genetics testing company—suffered a data breach in which the social security numbers (SSNs) of about 2.1 million people were exposed. The breach was made possible when the company acquired another firm nine years earlier, inheriting some databases that it didn’t know it had. Since these databases weren’t protected at the same level as active customer ones, an intruder on the network was able to access and exfiltrate the data.
Companies face various threats to their data. Ransomware is designed to encrypt data and demand a ransom for its recovery. Denial-of-service (DoS) attacks, lost devices, and broken hardware can also result in corporate or customer data being lost.
Frequent backups can help to protect against these threats by providing a means of restoring lost data. In fact, the mean recovery cost from a ransomware attack is cut nearly in half ($1.6 million vs $2.6. million) if the organization recovered from backups rather than paying the ransom.
Even if an organization has backups, this might not be enough. In the case of CloudNordic, the customers of the Denmark-based hosting company lost all of their data in a 2023 ransomware attack. The malware not only encrypted primary copies of the data but also two sets of backups, rendering it unrecoverable.
Passwords are commonly used to manage access to sensitive data. Password-based encryption and access controls ensure that an attacker needs to know a user’s password to access their data.
However, this also creates a single point of failure that introduces the risk of data loss. If a user forgets their password or leaves the company, the organization may lose access to all data protected by that password. If this is the only copy of valuable data, this could carry a significant cost for the business.
Data security can go wrong in a variety of different ways, leading to a costly, messy breach. However, the majority of data leaks are caused by a failure to implement fundamental cybersecurity best practices.
These are some of the most important steps that you can take to protect your data and that of your customers:
Enforcing the use of strong passwords is essential for data security.
To minimize the risk of account takeover attacks, passwords should be:
Companies can enforce strong password policies in various ways. Ensuring password length, randomness, and character sets is relatively easy. Organizations can also check password strength and uniqueness by comparing them to datasets of breached passwords.
Data can be in a few different states throughout its lifecycle. These include:
Data should be encrypted whenever possible. Encryption of data at rest and in transit is relatively easy since the data isn’t changing while in these states. Implementing file encryption and using Transport Layer Security (TLS) to protect network traffic prevents exposure of sensitive data in these states.
Encryption of data in use is more difficult because most encryption algorithms don’t allow calculations to be performed on encrypted data. While homomorphic encryption algorithms that allow encryption of data in use exist, they’re generally too inefficient for enterprise use.
As a result, encrypting data at rest and in transit provides as strong of protection as is feasible.
Access controls can go wrong in a few different ways. In some cases, organizations focus on securing the perimeter, allowing insiders access to everything within that boundary. In others, employees are granted administrative-level permissions on their own devices, even when they’re unnecessary.
The zero-trust security model encourages the use of least-privilege access controls. The principle of least privilege states that users, devices, applications, etc., should only have the rights and privileges that are essential for their role.
Implementing least privilege reduces the potential risks and impacts of an account takeover attack. Even if an attacker gains control over a user’s account—via compromised passwords, malware, or other means—the account can’t be used to steal or misuse data and other resources that the employee lacks the privileges to access in the first place.
Data retention and deletion are a complex issue for businesses. On the one hand, financial regulations mandate that a company retain records for a certain period of time.
On the other hand, data protection laws like the GDPR and CCPA/CPRA mandate that an organization discard customer data after it is no longer needed for the original purpose.
Balancing these requirements requires good data visibility and control managed by a clear data retention policy.
When designing and implementing a data retention and deletion policy, automation is key. Manually tracking data and creating backups or deleting unneeded data introduces the potential for oversights.
Some data security solutions offer the ability to automatically backup or destroy sensitive data in accordance with corporate policy.
In general, data breaches happen when data that is supposed to stay inside a company’s network makes its way outside. These leaks can happen in various ways, via email, cloud storage, USB drives, and more.
Data loss prevention policies and tools can help to protect against these data leaks.
Some key best practices include:
Many different mistakes can lead to a data breach, and implementing best practices can be a complex process. WinZip® Enterprise provides the tools that companies need to protect their data both inside and outside the corporate network.
When it comes to data encryption, the more granular, the better. Disk-level encryption and other general data encryption solutions increase the opportunities for an attacker to bypass the encryption and gain access to sensitive data.
For example, disk-level encryption is designed to protect against stolen devices and does nothing to defend against compromised user accounts or vulnerable applications.
WinZip Enterprise offers user-friendly encryption at the file level. With a swift command, it creates a secure password, encrypts your file, and shoots off an email with the password and file link—all set for your recipient.
By moving encryption to the file level, WinZip Enterprise ensures that decrypting some files on a disk doesn’t undermine the encryption of others.
The Advanced Encryption Standard (AES) is the official encryption algorithm endorsed by the U.S. National Institute of Standards and Technology (NIST). It offers three different private key strengths (129, 192, and 256 bit) and is considered the gold standard for encryption in both the public and private sectors.
In fact, the U.S. government only accepts AES as an encryption algorithm for Top Secret classified data.
WinZip Enterprise’s password-based encryption uses AES as the encryption algorithm. While all three AES key lengths are currently considered secure, users can select the level of security that they wish to use for their files.
Weak passwords are a common challenge for account and data security. If passwords are too short, use a restricted character set, or aren’t random, they’re too easy for an attacker to guess. All it takes is one broken password to cause a data breach.
While WinZip Enterprise can auto-generate passwords, users can also specify their own. However, to protect against weak passwords and ensure compliance with corporate security policies, the software can be configured to automatically enforce password requirements (minimum length, character sets, etc.).
Cloud-based file sharing is invaluable for collaboration. This is especially true with remote and hybrid work arrangements or for distributed companies.
However, cloud file sharing creates risks, especially if personal cloud accounts are involved. Data on personal clouds is outside of the company’s control, and the use of link-based sharing—whether on corporate or private clouds—can make sensitive data publicly accessible.
WinZip Enterprise makes it easy for organizations to enforce the use of approved corporate cloud accounts for file sharing. By streamlining the process of uploading files to the cloud and sharing them via email or other media, WinZip removes the incentive for users to default to insecure methods of sharing data with their colleagues or external partners.
Most people have at least one file that’s sat in their cloud storage untouched for years. This could be an itinerary for an old vacation, shared pictures, etc. With free cloud storage, there’s little need to go through and purge unneeded files on a regular basis.
However, these long-lived, forgotten files can be a problem for businesses, especially if they contain customers’ PII. Various data privacy laws mandate that this data be deleted when it is no longer needed; however, this is often easier said than done.
With WinZip, organizations and users can automatically enforce data deletion for their cloud data. When using WinZip to manage files stored in the cloud, users can define an expiration date at which the files will be automatically deleted.
87% of companies have multi-cloud deployments. Different cloud providers have different specialties and products available. Mixing and matching helps the company get the best available deal and optimize its infrastructure for the data and applications that it hosts.
However, using multiple clouds can make it difficult to move data between clouds and enforce security policies. As a result, companies can lose track of their data, and it might be exposed to attack.
WinZip seamlessly integrates with most major cloud platforms. Users can easily move files between their computers and multiple cloud environments. With WinZip’s built-in password-based file encryption, this offers a secure option for managing data in multi-cloud environments.
Passwords are lost for a variety of different reasons. Someone might forget or lose the password used to protect a critical document. Alternatively, an employee might leave the company, causing the organization to lose access to data encrypted with passwords known only to their former employee.
WinZip Enterprise balances the need for data security with the risk of data loss through its break-the-glass functionality. WinZip Enterprise applications can be preconfigured to include a master public key managed by the IT or security team.
Each time a file is encrypted with WinZip, recovery information is generated and encrypted with this public key. This way, if something goes wrong, the master key can be used to decrypt data even if the password has been lost or forgotten.
With personal emails, sending a message to the wrong person can be embarrassing. In a business context, that same mistake could lead to a data breach and legal trouble if the email contains sensitive customer information.
WinZip Enterprise helps to ensure that a typo in an email address doesn’t mean that legal needs to get involved. When configuring WinZip software, administrators can disallow personal email addresses when sharing files. This helps to ensure that corporate data stays inside the company and isn’t exposed—accidentally or intentionally—to the outside world.
Things go wrong. The company may be the victim of a ransomware or wiper attack that encrypts or deletes all of its data. A critical database server may fail, corrupting the data stored on its drives. A broken HVAC system could cause the company’s servers to overheat and melt.
In these situations and others, the company’s ability to recover from the incident depends on whether it has backup copies of lost data.
WinZip Enterprise enables an organization to schedule automated backups for all of its computers, storing data encrypted in the cloud where it can be used to restore data while minimizing losses.
Getting hacked and leaking sensitive data is, unfortunately, very easy. There are dozens of ways that data security can go wrong, and it only takes one mistake to become the victim of an expensive and damaging breach.
However, a solid data security program can help with avoiding these pitfalls.
In a rapidly evolving cyber threat landscape, the risks of poor data security loom large, demanding our utmost attention. The consequences of a data breach extend far beyond financial losses, reaching into the realms of brand damage, lost business, legal action, and regulatory penalties.
As exemplified by the increasing frequency of breaches, the theoretical strength of encryption and access controls often falters in reality.
The onus is on organizations to fortify their defenses and address the vulnerabilities highlighted in this report. From combating weak passwords to reevaluating access controls, each step toward robust data security is a stride away from becoming another statistic in the data breach landscape.
Let this e-book serve as a roadmap for safeguarding your organization's critical data, ensuring resilience against the ever-present cyber threats. In the face of cyber adversaries, proactive defense is our strongest shield.
That’s where WinZip Enterprise comes in. With its advanced encryption features, WinZip Enterprise ensures that sensitive information, whether at rest, in transit, or in the cloud, remains impervious to unauthorized access. This is particularly invaluable for IT (security) managers working under stringent data protection laws and regulations.
By seamlessly integrating into your workflow, WinZip Enterprise becomes the single pane of glass through which you can manage, protect, and transport sensitive files on removable media, thereby mitigating the risks associated with distributed workforces and the usage of removable media.
With WinZip Enterprise, you not only gain fail-safe security measures but also empower your IT team with enforceable security controls, logging capabilities, and FIPS-compliant encryption, providing a comprehensive shield against the multifaceted challenges posed by the ever-evolving cyber threat landscape.