You've probably heard in the news that large companies and government organizations are losing millions of dollars and sensitive information because hackers and other threat actors have stolen their data.
But what you might not know is that they are targeting individuals like you, too.
Many victims have lost thousands of dollars because the information they stored on their computers was compromised.
Thankfully, there are precautions you can put in place to keep your data safe and protected.
Here's how you can password-protect and encrypt your files with WinZip.
That way, even if someone manages to steal your data, it'll remain useless as it's locked and can only be opened with the correct password. Download WinZip to password-protect your files.

A Zip file combines one or more files into a smaller compressed archive. This offers an ideal way to share large files and keep related files together.
An encrypted Zip file adds a layer of protection to the Zip file, securing its contents and ensuring that only authorized users can see them.
An encrypted zip file achieves that extra layer of security through complex algorithms.
When you send an encrypted file, an encoding algorithm is applied to scramble the data, ensuring it's unreadable without the decryption key.
This key typically comes as a passcode, passphrase, or PIN.
Once you type in the key, WinZip will decrypt the Zip file, allowing you to read its contents.
While you may think you only need file encryption to protect your work files, you also need it to secure your personal data and information.
At the very least, files that contain personally identifiable data, like your social security number or pictures you don't want to spread online for people to see, should be kept in an encrypted zip file.
Furthermore, you should encrypt financial information and records, legal documents, confidential projects, and backups and archives.
It's easy to assume that all forms of data security will protect you equally. However, this assumption could not be farther from the truth.
For example, DES (Data Encryption Standard), first published in 1975, is a widely used algorithm for protecting data.
But because of its age and its reliance on a short 56-bit key, it cannot withstand the modern threats we're facing today.
That's why you should use modern algorithms like AES (Advanced Encryption Standard).
As the name implies, this encryption method is far more advanced than DES because of its key-length options.
AES lets you pick between 128-bit, 192-bit, and 256-bit keys, significantly boosting your protection.
In layman’s terms, the longer key makes its algorithm far more complex and challenging to crack.
It's also exponentially faster, so a robust yet efficient encryption system protects you.
Although many use password protection and encryption synonymously, they're two distinct concepts—the former merely prevents access to content, while the latter scrambles the content completely.

Password locking refers to the process of protecting data with a string of symbols.
By adding password protection, your files cannot be accessed without the corresponding code.
However, passwords alone cannot completely protect your data.
If a third party bypasses your password protection, they can still view the files and other information behind it.
Encryption goes beyond preventing unauthorized access to your files—instead, it makes them totally unreadable by using an encryption algorithm.
This means that even if someone bypasses the password of an encrypted file, they will only see a bunch of random digits, letters, and symbols.
To open an encrypted folder, you must have the decryption key to make sense of all the gibberish inside it.
And while it's theoretically possible to crack an encrypted file, it would take a supercomputer hundred, if not thousands, of years to brute force it.
Given that, it's always better to encrypt your files.
As long as someone trying to access your files does not have your key, they won't be able to see its content.
Nevertheless, whether you're using simple password protection or AES, you should always use a strong password.
After all, your data security is only as strong as its weakest link.
A weak password is prone to various attacks, including dictionary hacks, brute-force attacks, phishing, rainbow table attacks, and more.
Here’s a helpful WinZip resource for how to password protect a Zip file.
Unfortunately, there's no easy way to encrypt files straight from Windows. If you want to protect your files, you should use a trustworthy app that you know won't steal your data—like WinZip.
You can easily password-protect and encrypt your files on Windows in just a few steps. Here's how:
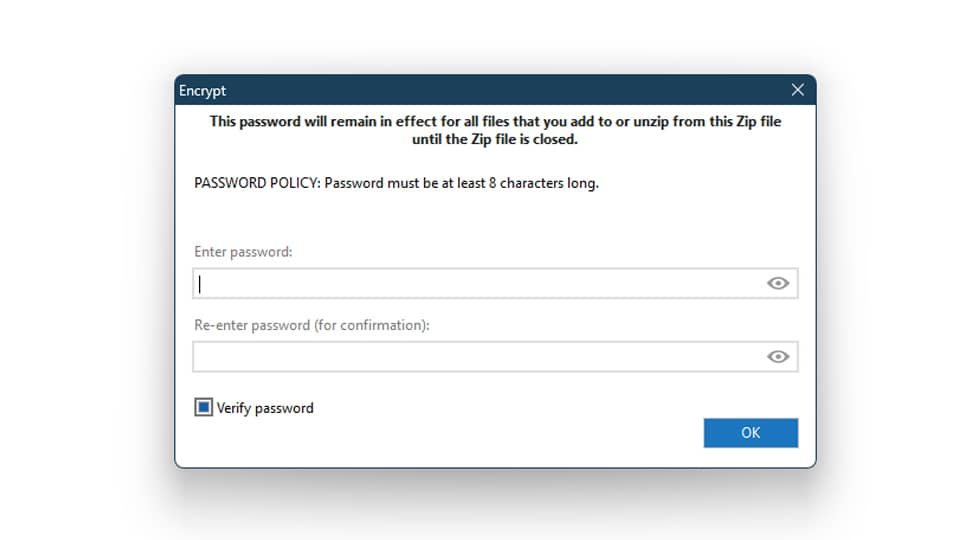
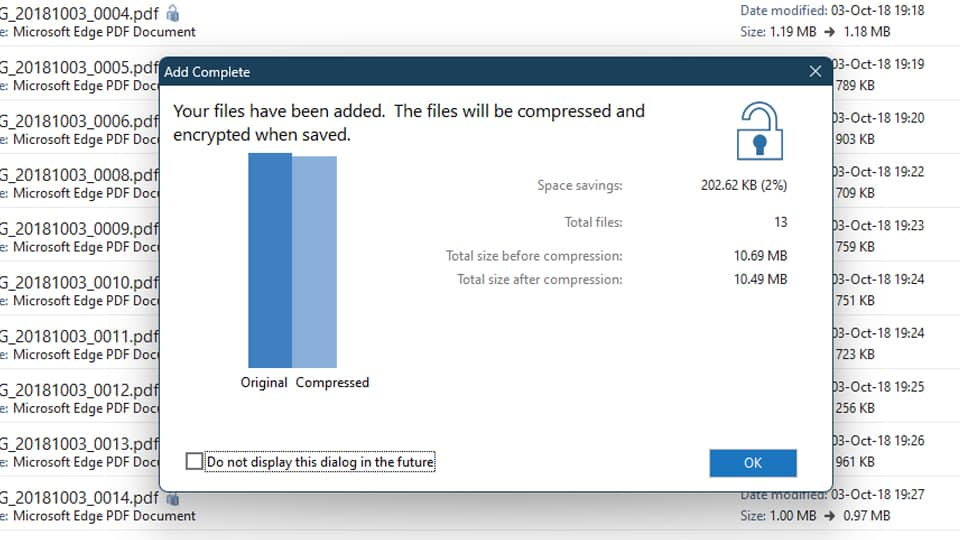
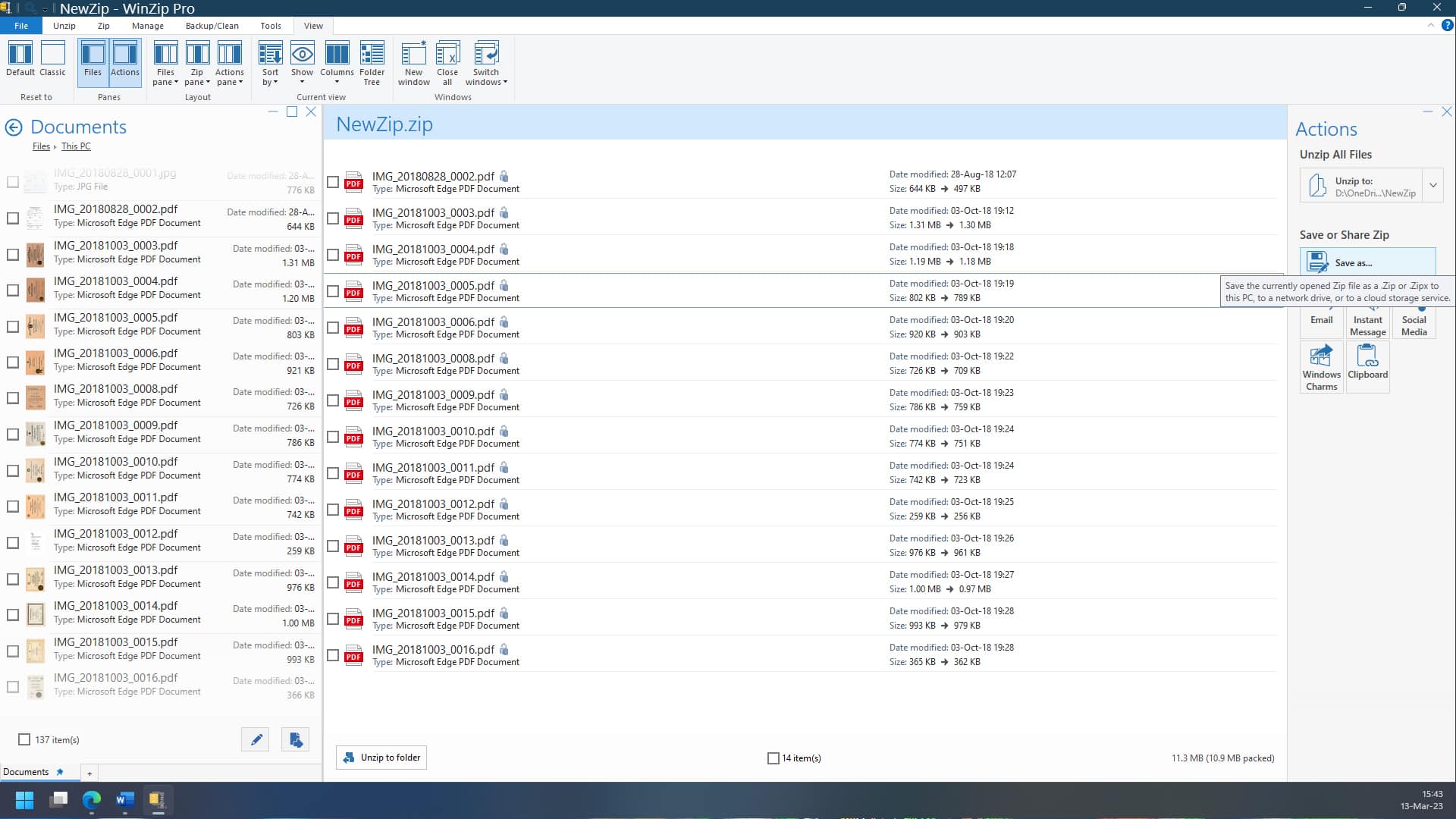
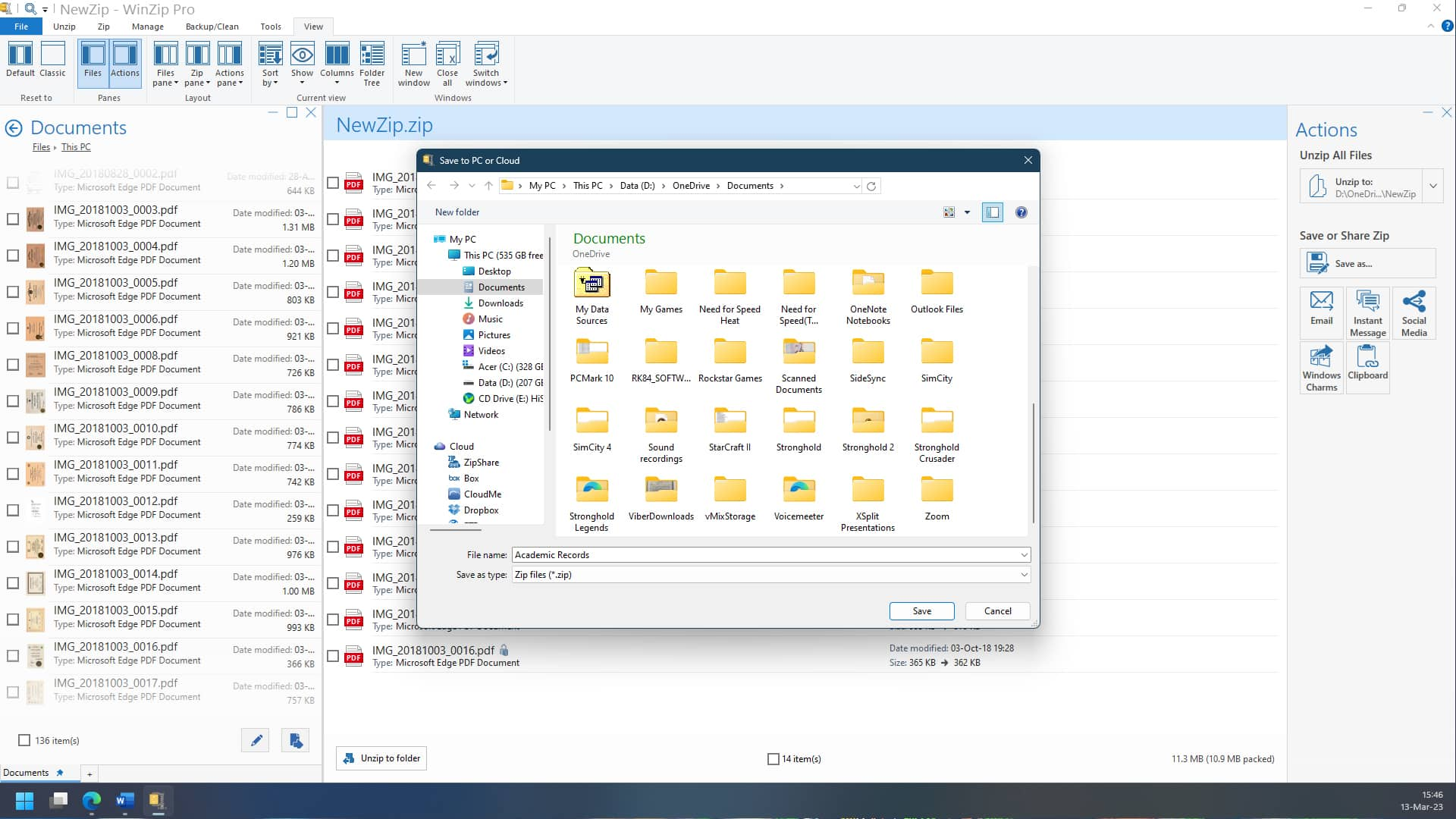
And with that, your selected files are now encrypted and password protected.
We recommend you delete the original unencrypted files for maximum security to ensure they're not compromised.
Important Note: You should remember or store your password in a safe place to encrypt your files. If you forget your password, recovering the protected files is extremely difficult, if not impossible.
Now that your data is protected, here's how to open it.
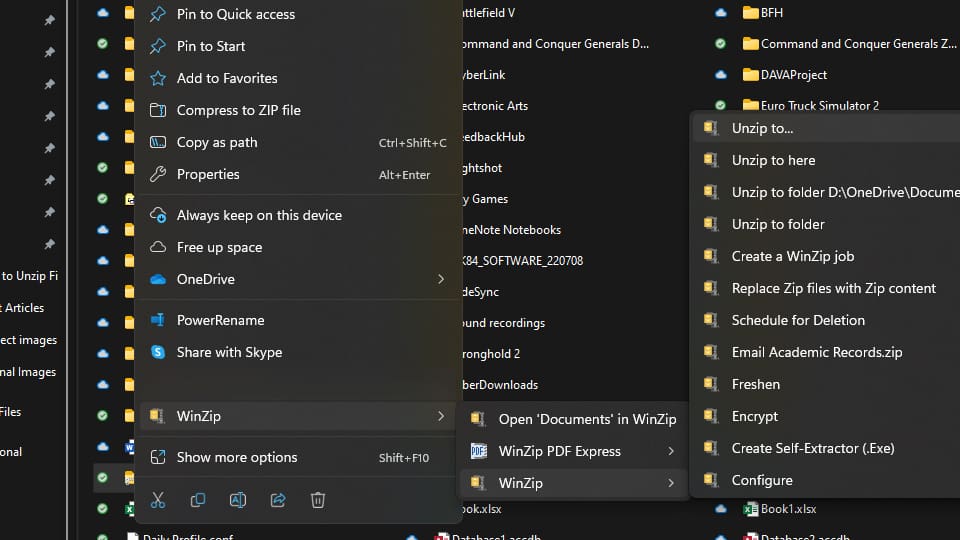
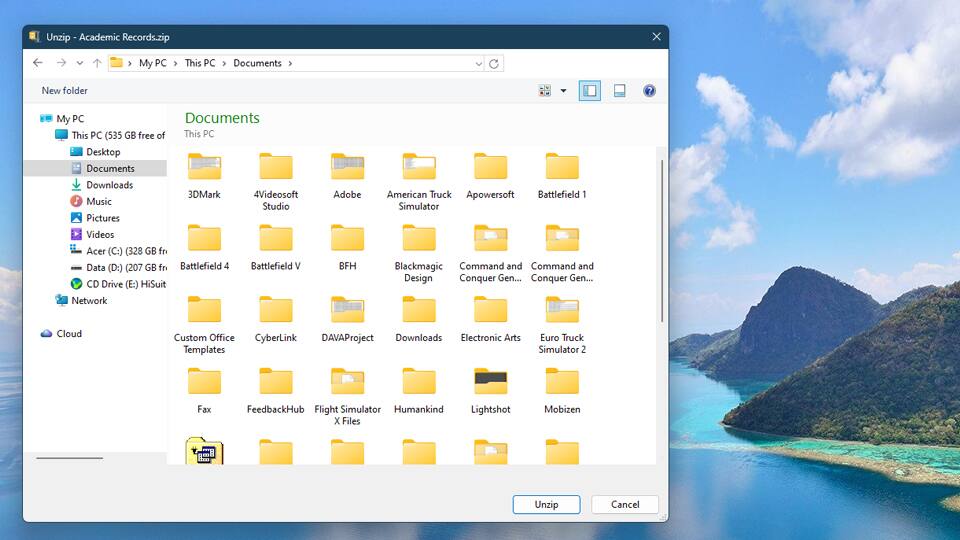
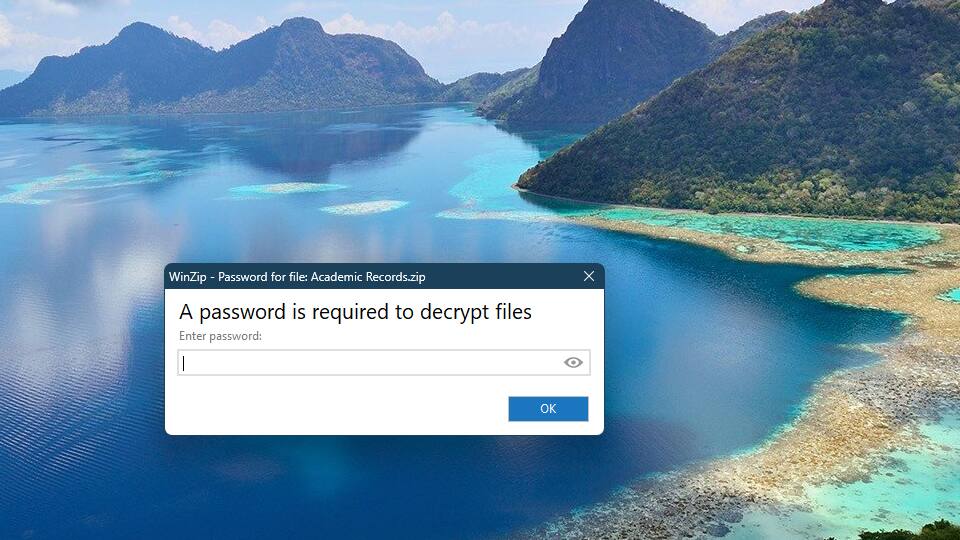
Note: You can still open the encrypted zip file on File Explorer, but Windows will not understand it because it uses WinZip encryption. To decrypt the file, you need to use WinZip. Download WinZip for free today.
Password protecting and encrypting your files looks a little different on macOS. You can do both of these without additional software, but you must do it manually through Terminal.
Terminal can be a little complex for first-time users. You need to type commands yourself, meaning there's a chance for typos and errors. But there's no need to worry.
Here's a step-by-step guide on how to use Terminal to password-protect your files on Mac.
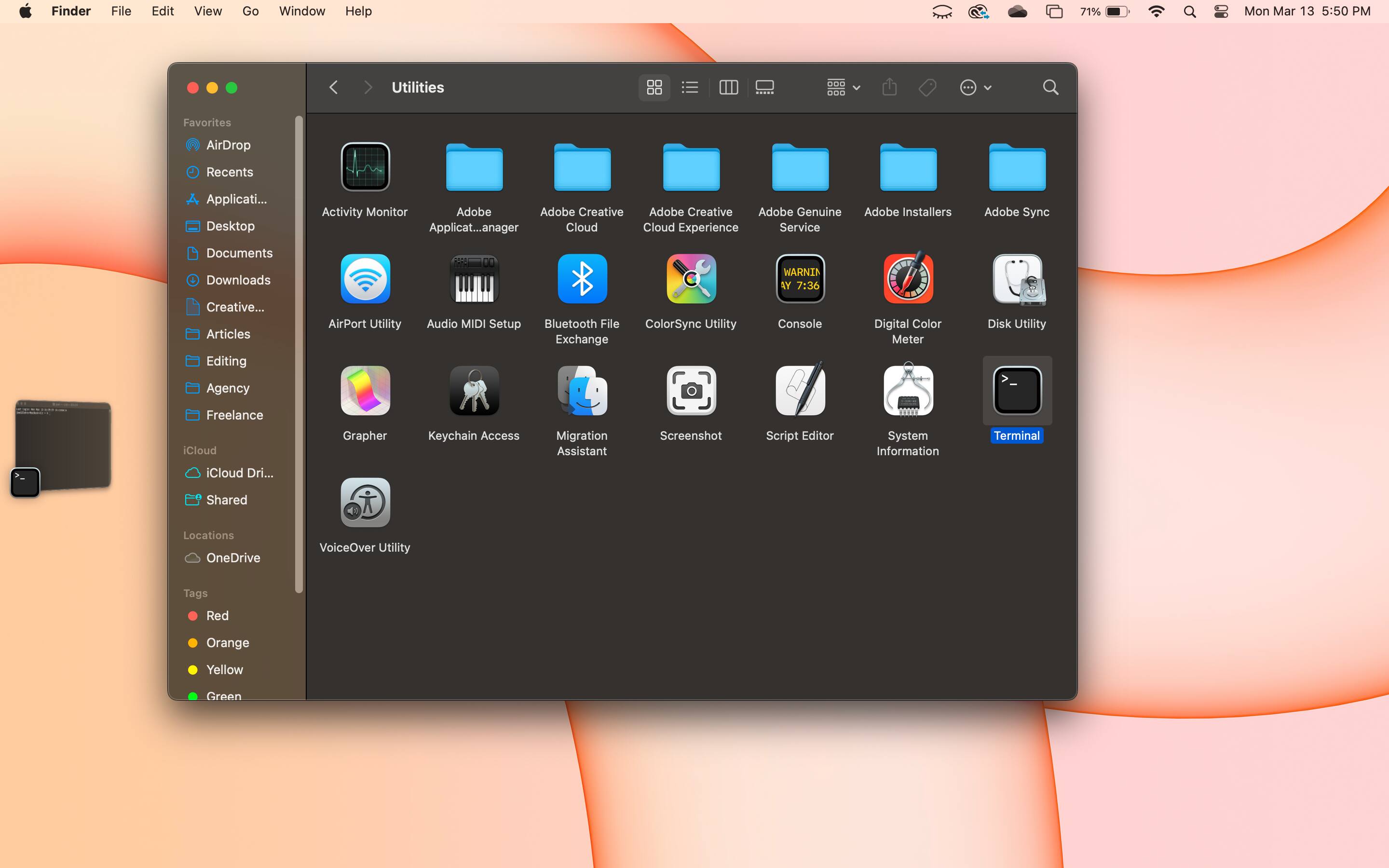
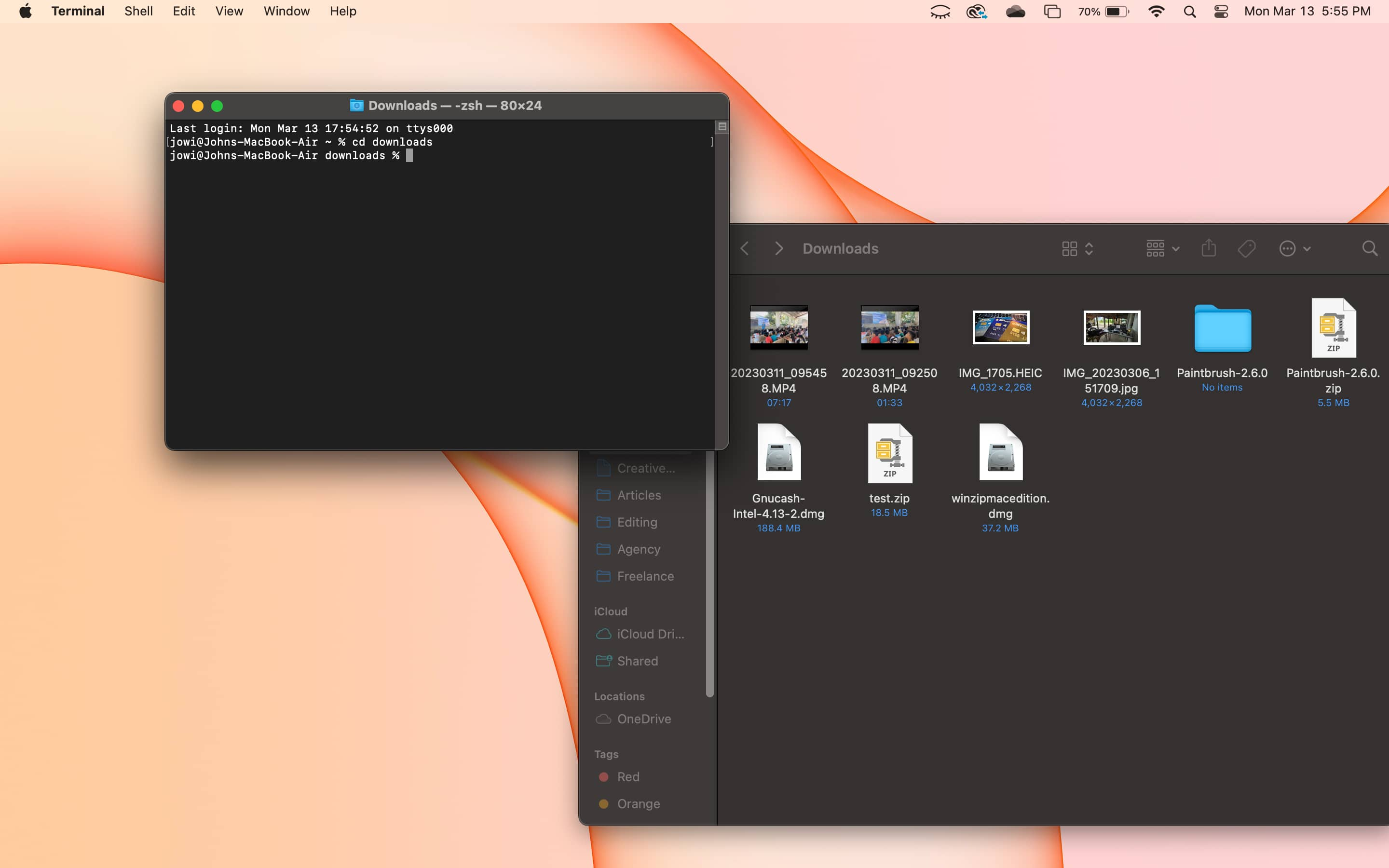
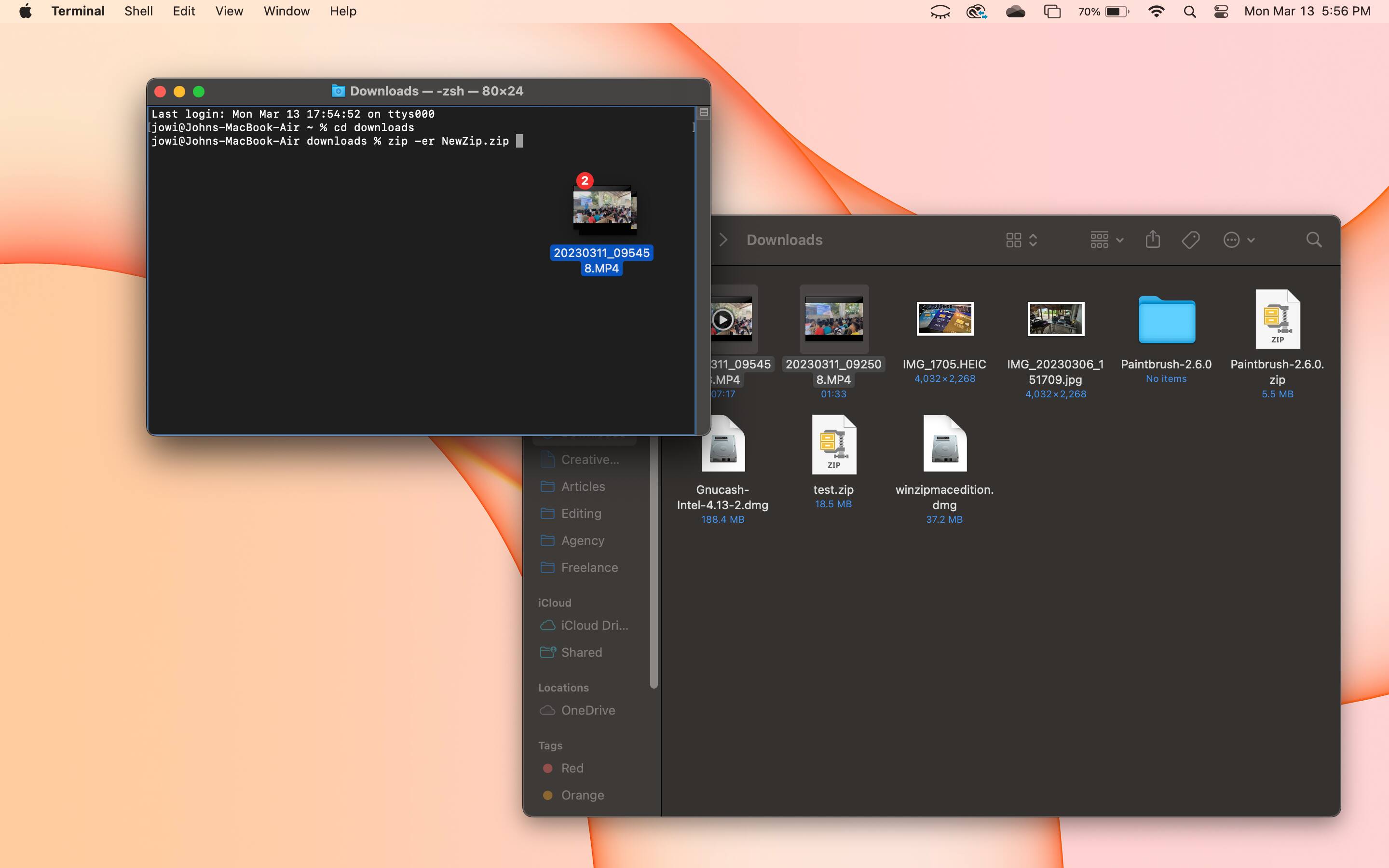
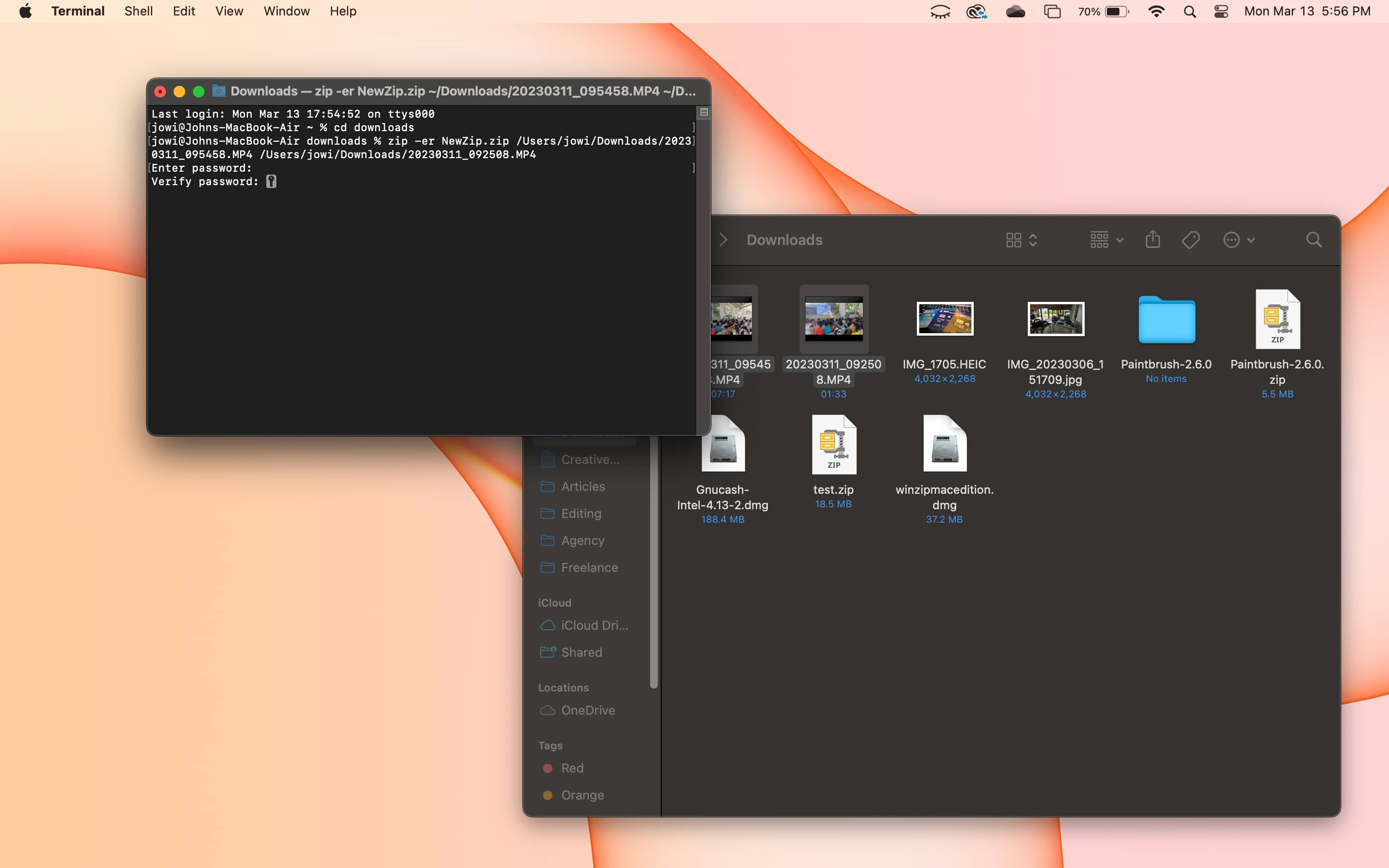
If you follow these steps, you will have successfully created an encrypted zip file or folder.
However, it is common to make a few mistakes, and it will probably take a few tries before you can easily encrypt files in the Terminal.
Furthermore, it takes some time to zip files, especially large ones.
Whether you use WinZip or the macOS Archive Utility to open this encrypted file, you must provide the password to unlock it.
If you frequently create encrypted files and wish to do it in fewer steps, you can use WinZip.
This app allows you to easily create multiple encrypted files and folders, ensuring your data is safe and protected. Best of all, you can try WinZip for free.

FIPS (Federal Information Processing Standard) 140-2 confirms the effectiveness of hardware and software cryptography by ensuring they adhere to a standard set by the US federal government.
You should ensure your encryption algorithm is FIPS 140-2 compliant for maximum protection.
There are several ways to decrypt a file; typically, you'd need a password, but you also usually need a decrypting app specific to the algorithm used, too.
Thankfully, WinZip lets you decrypt the most common encrypted Zip and Zipx files.
Here's how to decrypt a file using WinZip. First, open the encrypted file with WinZip Pro.
Then, click and drag the documents to your destination folder.
Finally, type in the password and click OK.
You can password-protect an Excel file to secure its contents. Here's how to do it from inside the office application:
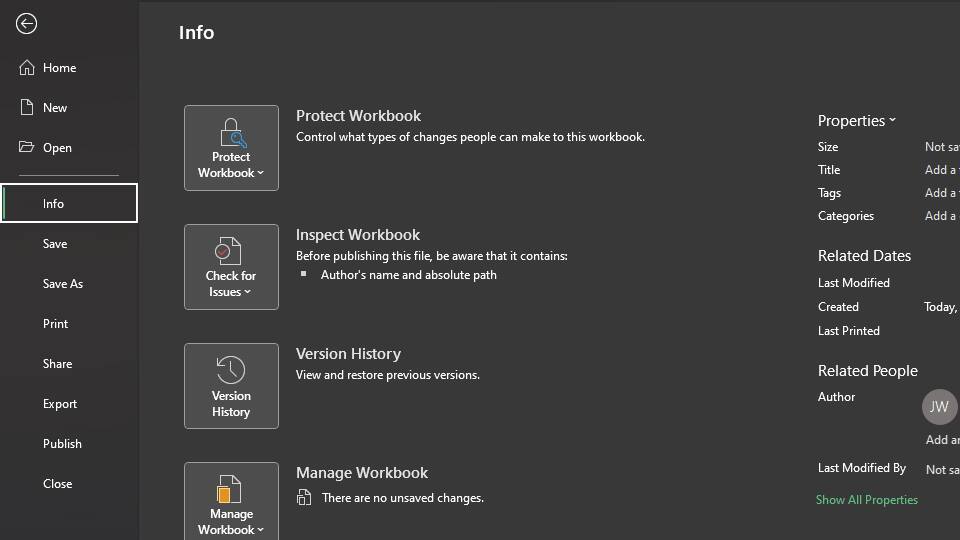
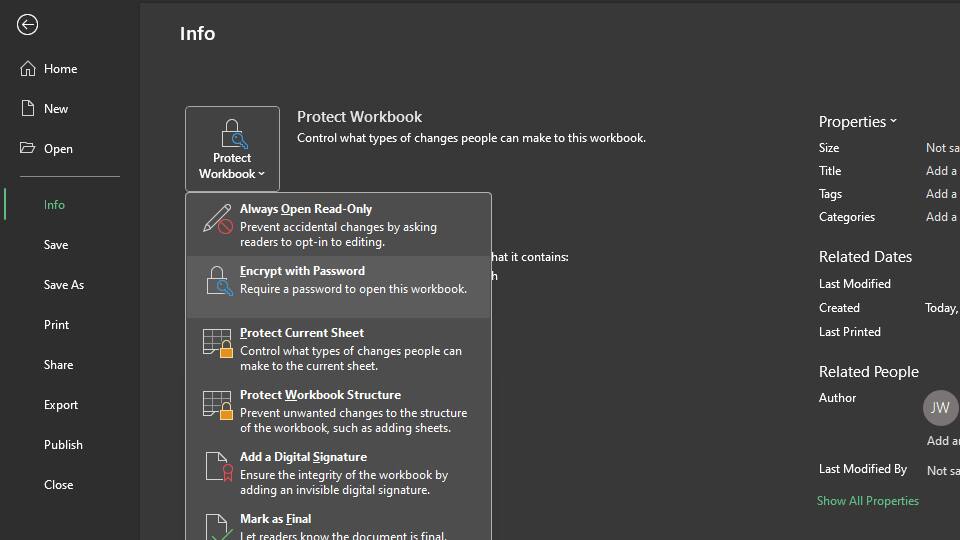
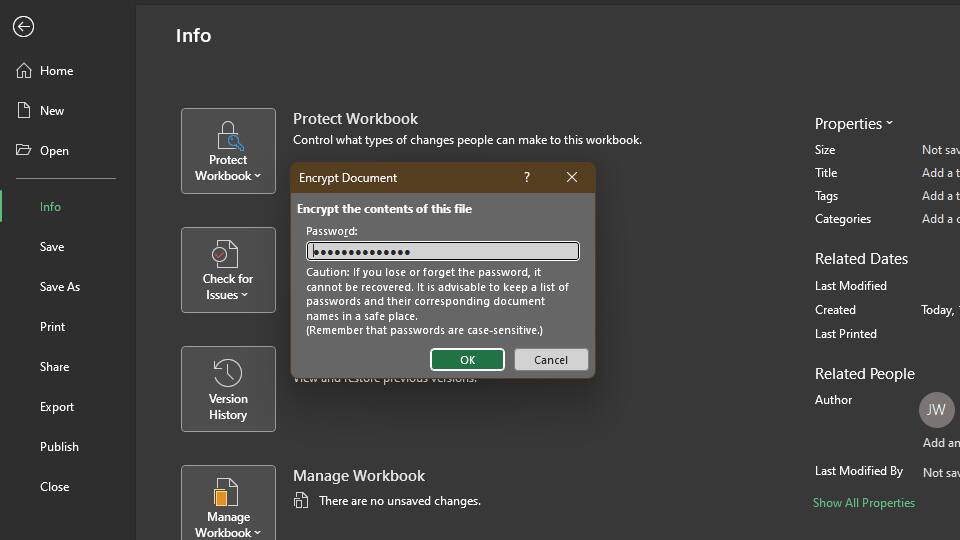
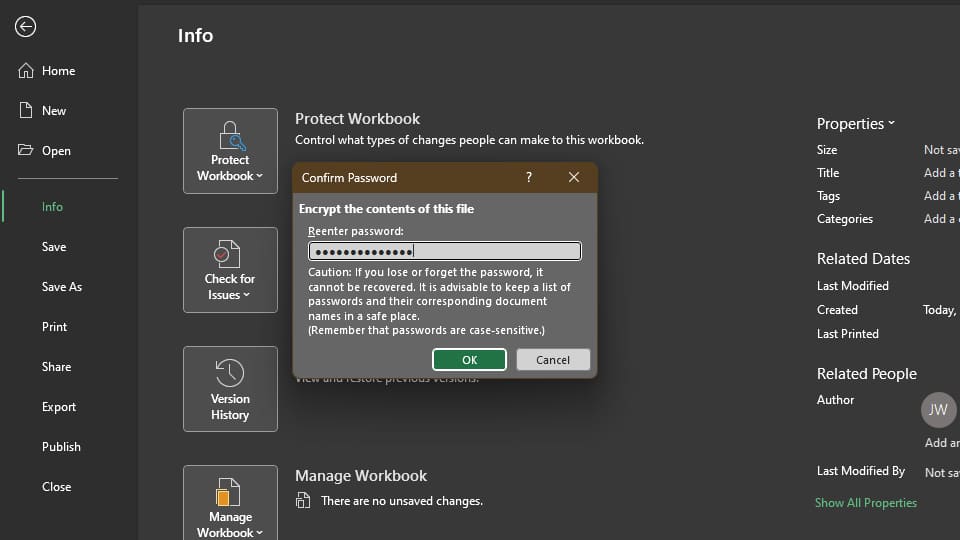
After following these steps, your Excel file is now password-protected. You should also see it in the Info window, where you should see Protect Workbook: A password is required to open this workbook.
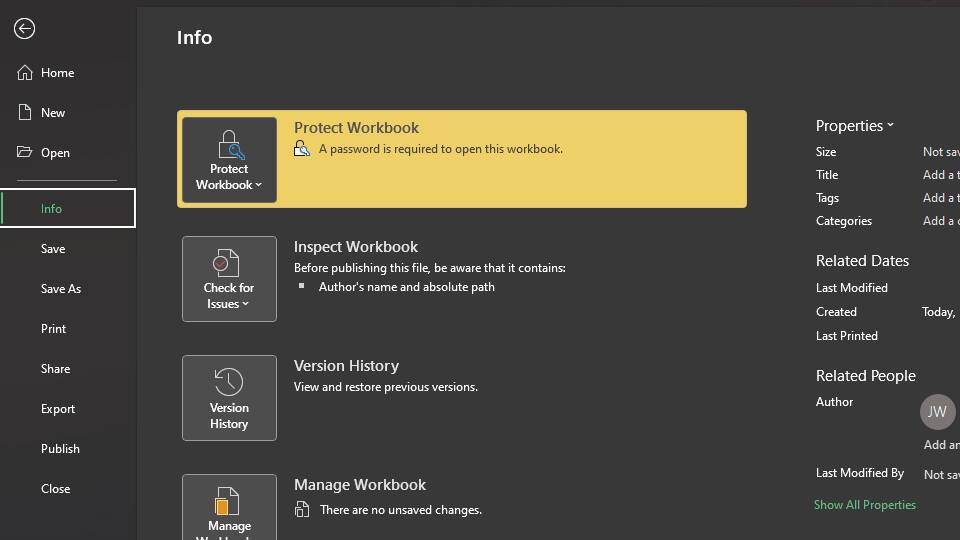
These steps ensure that only authorized users can open your Excel file. However, you must remember your password or keep a copy safely hidden away. If you forget your password or lose your copy, recovering your Excel file is almost impossible.
You cannot password-protect Word documents in older versions of Microsoft Word.
But with Microsoft 365 and Word for Mac 2011, you can encrypt your Word files on the app.
Here's how:
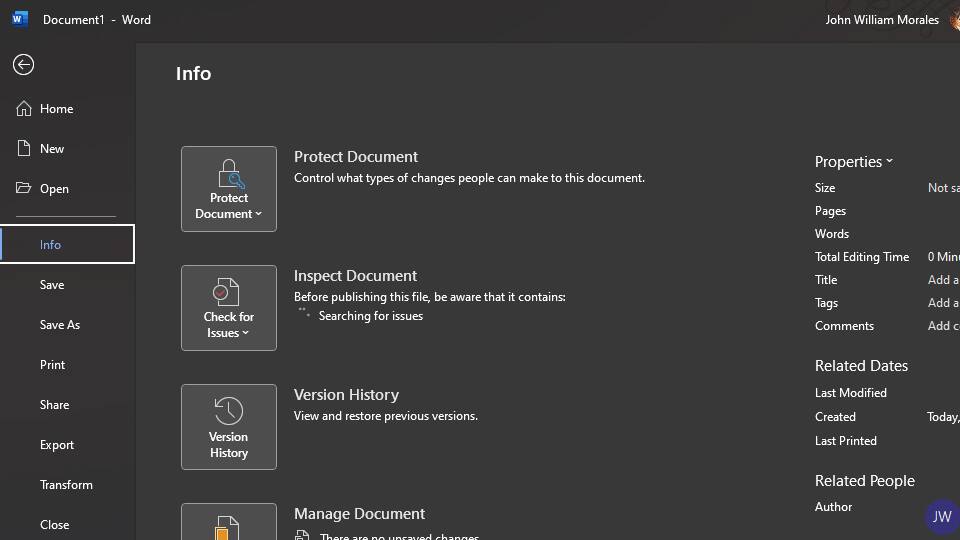
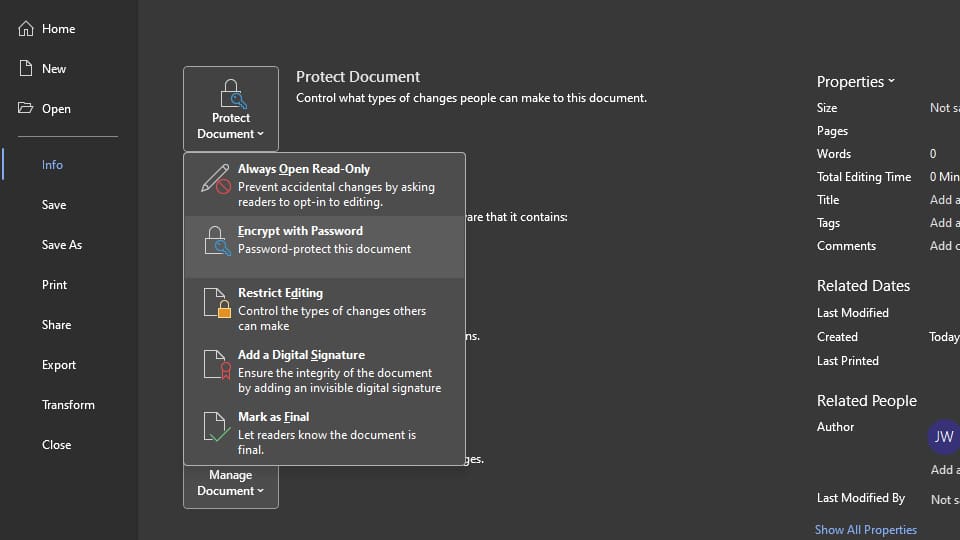
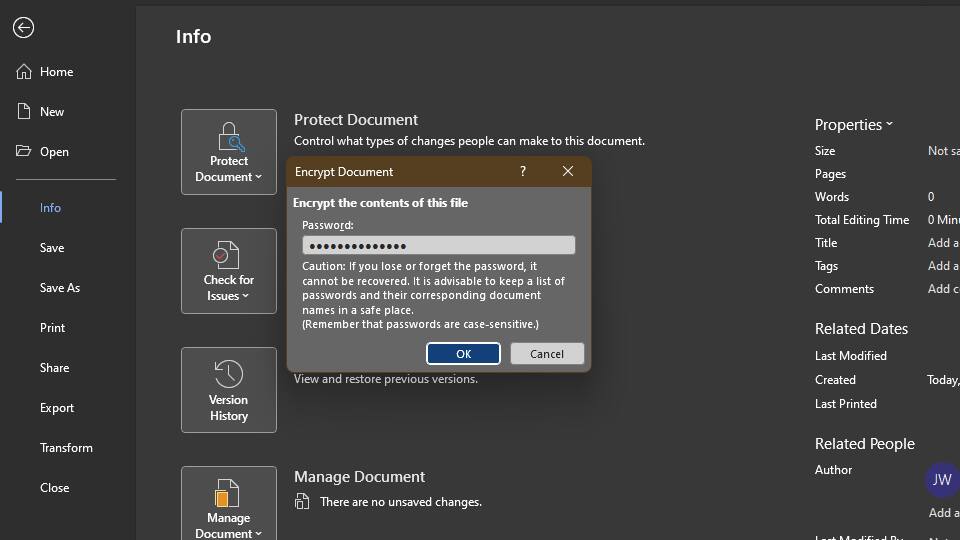
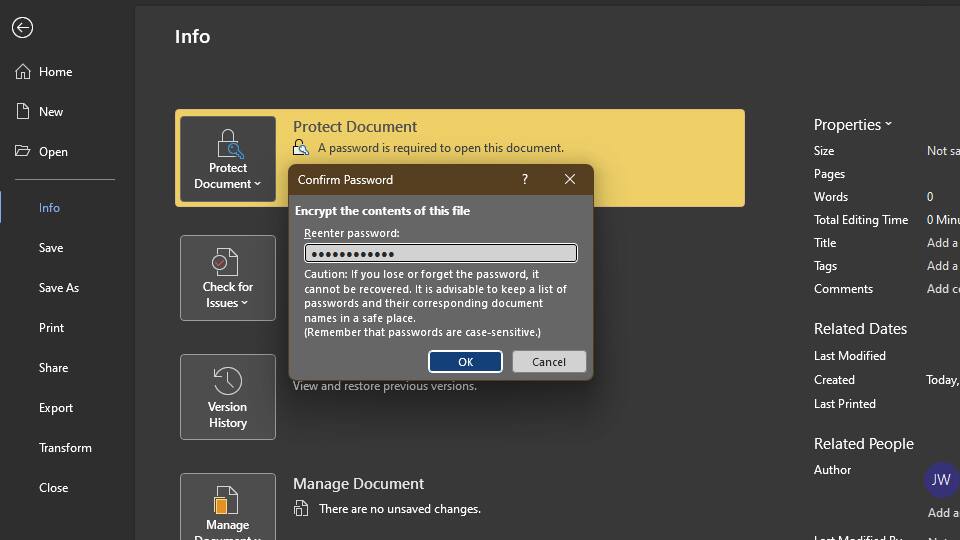
And with that, your Microsoft Word file is now password-protected. You should see Protect Document highlighted with yellow to confirm that your file requires a password to open.
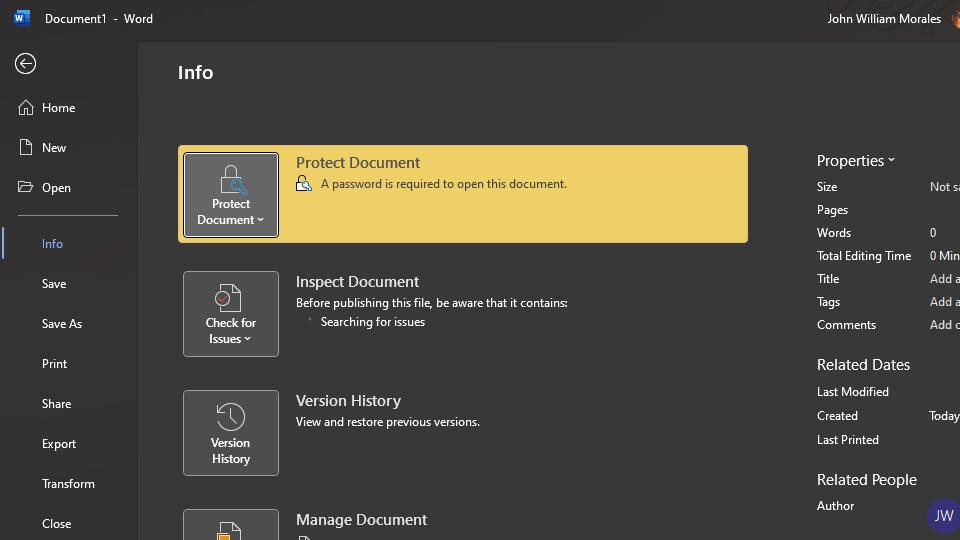
Much like a password-protected Excel file, you should remember your password or keep a copy of it safely stored.
If you forget your password, you won't be able to recover your encrypted Word file.
Companies pay millions of dollars to acquire information.
Most "free" sites may not charge you money, but they come with a cost—your data.
While you may not think they're worth much, your privacy and security are of utmost importance and should be treated as such.
In this modern world, password protection and encryption should be standard practices. Make it a part of yours and Download WinZip for free today.